Ssh Config Ssh Key
This topic covers the Windows-specific configuration for OpenSSH Server (sshd).
SSH provides an authentication mechanism based on cryptographic keys, called public key authentication. One or more public keys may be configured as authorized keys; the private key corresponding to an authorized key serves as authentication to the server. Sshdconfig is the OpenSSH server configuration file. How to configure and troubleshoot. Avoid getting accidentally locked out of remote server. Read reviews, compare customer ratings, see screenshots, and learn more about SSH Config Editor. Download SSH Config Editor for macOS 10.13 or later and enjoy it on your Mac.
OpenSSH maintains detailed documentation for configuration options online at OpenSSH.com, which is not duplicated in this documentation set.
Ssh Config Ssh Key Mac
Configuring the default shell for OpenSSH in Windows
The default command shell provides the experience a user sees when connecting to the server using SSH.The initial default Windows is the Windows Command shell (cmd.exe).Windows also includes PowerShell and Bash, and third party command shells are also available for Windows and may be configured as the default shell for a server.
To set the default command shell, first confirm that the OpenSSH installation folder is on the system path.For Windows, the default installation folder is SystemDrive:WindowsDirectorySystem32openssh.The following commands shows the current path setting, and add the default OpenSSH installation folder to it.
| Command shell | Command to use |
|---|---|
| Command | path |
| PowerShell | $env:path |
Configuring the default ssh shell is done in the Windows registry by adding the full path to the shell executable to ComputerHKEY_LOCAL_MACHINESOFTWAREOpenSSH in the string value DefaultShell.
As an example, the following Powershell command sets the default shell to be PowerShell.exe:
Windows Configurations in sshd_config
In Windows, sshd reads configuration data from %programdata%sshsshd_config by default, or a different configuration file may be specified by launching sshd.exe with the -f parameter.If the file is absent, sshd generates one with the default configuration when the service is started.
The elements listed below provide Windows-specific configuration possible through entries in sshd_config.There are other configuration settings possible in that are not listed here, as they are covered in detail in the online Win32 OpenSSH documentation.
AllowGroups, AllowUsers, DenyGroups, DenyUsers
Controlling which users and groups can connect to the server is done using the AllowGroups, AllowUsers, DenyGroups and DenyUsers directives.The allow/deny directives are processed in the following order: DenyUsers, AllowUsers, DenyGroups, and finally AllowGroups.All account names must be specified in lower case.See PATTERNS in ssh_config for more information on patterns for wildcards.
Ssh Install Ssh Key
When configuring user/group based rules with a domain user or group, use the following format: user?domain*.Windows allows multiple of formats for specifying domain principals, but many conflict with standard Linux patterns.For that reason, * is added to cover FQDNs.Also, this approach uses '?', instead of @, to avoid conflicts with the username@host format.
Work group users/groups and internet-connected accounts are always resolved to their local account name (no domain part, similar to standard Unix names).Domain users and groups are strictly resolved to NameSamCompatible format - domain_short_nameuser_name.All user/group based configuration rules need to adhere to this format.
Examples for domain users and groups
Examples for local users and groups
AuthenticationMethods
For Windows OpenSSH, the only available authentication methods are 'password' and 'publickey'.
AuthorizedKeysFile
The default is '.ssh/authorized_keys .ssh/authorized_keys2'. If the path is not absolute, it is taken relative to user's home directory (or profile image path). Ex. c:usersuser. Note that if the user belongs to the administrator group, %programdata%/ssh/administrators_authorized_keys is used instead.
ChrootDirectory (Support added in v7.7.0.0)
This directive is only supported with sftp sessions. A remote session into cmd.exe wouldn't honor this. To setup a sftp-only chroot server, set ForceCommand to internal-sftp. You may also set up scp with chroot, by implementing a custom shell that would only allow scp and sftp.
HostKey
The defaults are %programdata%/ssh/ssh_host_ecdsa_key, %programdata%/ssh/ssh_host_ed25519_key, %programdata%/ssh/ssh_host_dsa_key, and %programdata%/ssh/ssh_host_rsa_key. If the defaults are not present, sshd automatically generates these on a service start.
Match
Note that pattern rules in this section. User and group names should be in lower case.
PermitRootLogin
Not applicable in Windows. To prevent administrator login, use Administrators with DenyGroups directive.
SyslogFacility
If you need file based logging, use LOCAL0. Logs are generated under %programdata%sshlogs.For any other value, including the default value, AUTH directs logging to ETW. For more info, see Logging Facilities in Windows.
Not supported
The following configuration options are not available in the OpenSSH version that ships in Windows Server 2019 and Windows 10 1809:
- AcceptEnv
- AllowStreamLocalForwarding
- AuthorizedKeysCommand
- AuthorizedKeysCommandUser
- AuthorizedPrincipalsCommand
- AuthorizedPrincipalsCommandUser
- Compression
- ExposeAuthInfo
- GSSAPIAuthentication
- GSSAPICleanupCredentials
- GSSAPIStrictAcceptorCheck
- HostbasedAcceptedKeyTypes
- HostbasedAuthentication
- HostbasedUsesNameFromPacketOnly
- IgnoreRhosts
- IgnoreUserKnownHosts
- KbdInteractiveAuthentication
- KerberosAuthentication
- KerberosGetAFSToken
- KerberosOrLocalPasswd
- KerberosTicketCleanup
- PermitTunnel
- PermitUserEnvironment
- PermitUserRC
- PidFile
- PrintLastLog
- RDomain
- StreamLocalBindMask
- StreamLocalBindUnlink
- StrictModes
- X11DisplayOffset
- X11Forwarding
- X11UseLocalhost
- XAuthLocation
Managing remote servers requires either a very good memory to remember connection options like usernames, remote addresses, ports and further details or a good way to document all the details for each server.
The SSH config file should be your helping hand to control and simplify SSH connections. If you didn't have any SSH client installed yet, please go ahead and do it. OpenSSH is our tool of choice.
Complicated Connections
Connecting to a remote server via SSH requires a username, server url or IP address and the SSH server port listening for connections. Let's look at a specific example. Assuming your server url is yourserver.url with user marcus on port 2222.
Your connection command looks like this:
All parameters are required to pass within the connection string.
Simplify with SSH Config File
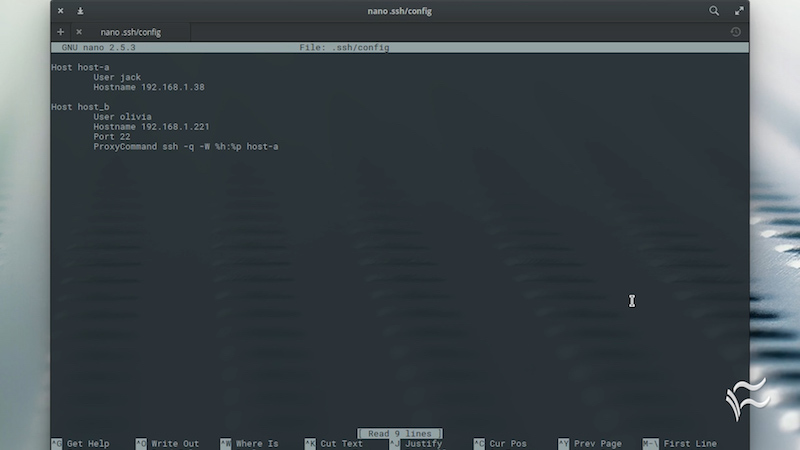
The SSH config file isn't created automatically while installing SSH on your machine. The config file needs to be placed into your .ssh folder. By default, the location is ~/.ssh. Let's create the config file using nano command line editor. Since nano is Linux specific, you can use any other editor of your choice.
This command opens the nano editor with a blank file. Saving to disk will create the desired SSH config file.
We define the file content using the key-value system. Each key-value-pair is stated in a separate line. A key gets its value assigned by separating both by either whitespace or equal sign or a combination of equal sign with spaces. The SSH clients interpret all statements identical.
Each configuration in your config file is initiated by the keyword Host followed by an identifier.
Common SSH configuration options
- HostName: the hostname or IP address of your remote server. You can skip this definition if the
Hostidentifier already specifies the actual hostname you want to connect with. - User: the connection username.
- Port: the port where your remote SSH server is listening for connections. Default value
22.
The options above describe the basic configuration for an entry in the SSH config file. There are additional SSH connection items and tweaks which can be used for more complex setups.
General Tweaks and SSH connection items
- Compression: a useful option for (very) slow connections.
- ServerAliveInterval: use this option to let both peers stay in contact and avoid session closes due to SSH timeouts. Configure this option to let SSH send a packet to keep the connection between client and server alive. Also, you can use this option to know if your unreliable connection is still alive.
- StrictHostKeyChecking: this option is used to configure whether SSH automatically adds hosts to the
~/.ssh/known_hostsfile. By default, you're asked to confirm the addition to the known hosts. The default value can be annoying connecting to multiple different hosts, so you may want to set this to no and add every connected remote host to known hosts automatically.
Actually, there are more options to configure SSH. You can keep those items listed above in mind and in case you run into issues with your SSH connections, change the values and check whether they improve.
Linux Ssh Config
Complete configuration entry example:
Ssh Config Password
Of course you can define multiple entries in your config file. Just separate them by an empty line
The second example entry omits the HostName definition because it's already set as Host identifier.
Just save the file and leave nano. Your created file will be recognized by your SSH client for future connections.

Connect Painlessly
From now on, you can use the defined Host identifier for any connection to your remote server.
Your SSH client parses the config file and matches the defined Host identifier values with your provided identifier. In case they match, the specific configuration gets automatically loaded from the config file.
That's all the magic! Enjoy the simplification of your SSH configuration.
Additional Ressources
